Driving The Cyber Crime Pandemic
By : Krishna Anindyo | Thursday, June 04 2020 - 15:30 IWST
Business Email Compromise (BEC)
INDUSTRY.co.id - In its early days, Business Email Compromise (BEC) attacks typically began with hacking or spoofing email accounts of CEOs or CFOs of businesses, and then requesting fund transfers to accounts controlled by the criminals.
Over the years, these attacks have grown in sophistication, mostly in the social engineering aspect. Rather than targeting the companies directly, attacks now target customers, HR departments, suppliers, related accountants, and law firms, and even tax authorities.
In addition to directly generating or diverting currency transactions, BEC attacks have also been used to fraudulently purchase gift cards, divert tax returns, and even transfer millions of dollars’ worth of hardware and equipment into the control of cybercriminals.
To help with their social engineering attempts, criminals love to tap into interest in major current events or news stories. Right now, they have the perfect vehicle for scams with the COVID-19 pandemic. The new working conditions enforced by the global outbreak has triggered a spike in BEC scams, because more remote working means more opportunities to catch users off guard.
Check Point Research recently showed a 30% increase in COVID-19 related cyber-attacks over the first two weeks of May, many of which involved email scams. On average, there were 192,000 coronavirus-related cyber-attacks documented per week.
Multiple incidents have been reported of government agencies and medical services, who, while attempting to procure medical equipment, transferred funds to fraudulent brokers prior to receiving the items, only to learn that the equipment did not exist, and that the funds are unrecoverable.
Let us look at the components of a basic BEC attack. An attacker typically constructs an email that impersonates a high-level executive of a company – either by hacking into the organisation’s email system, or by designing a legitimate-looking fake – and sends it to an employee, requesting a transfer of money to a bank account under the attackers’ control. This is often done with the excuse of urgency or communication problems to prevent the manager from communicating in alternative ways.
The attacker spoofs the source email address – as the basic SMTP protocol does not provide a sender validation mechanism, attackers can use either dedicated or publicly exposed SMTP servers to send emails with a spoofed sender address.
The attacker sends emails from the authentic email account of the impersonated victim by gaining control of their email account through phishing, credentials theft, or other means.
The attacker sends an email using a look-alike domain, which they register. In this case, the domain differs from the authentic address by a minor detail, such as sending an email from “example” rather than “example”.
BEC scams hit all sectors of commerce, from real-estate to art, government, municipalities and even the military. In one such fraud that was exposed in 2019, a US defence contractor was tricked into sending equipment for a fake order worth over US$10 million, including US$3.2 million in highly sensitive communications interception equipment.
The attacker sent a phony purchase order using a fake Yahoo! email address ending in “navy-mil.us.” The equipment was shipped and received in an office space which, upon further investigation, revealed the identity of the person who contracted it, leading to his arrest.
The success of such BEC frauds requires, in addition to the fake email account, detailed knowledge of the identity of the officials to contact, the tone and phrasing of the purchase order and communication jargon, and knowledge of the right equipment to order.
Often, these sophisticated attacks are not conducted by a single individual but by an infrastructure typical to organised crime. Operations demand bank accounts to be established, which often requires the use of stolen identities obtained in underground markets or stolen in separate operations.
Stolen funds must be withdrawn by multiple individuals and transactions, which involves complex logistics of money mules, often in international operations.
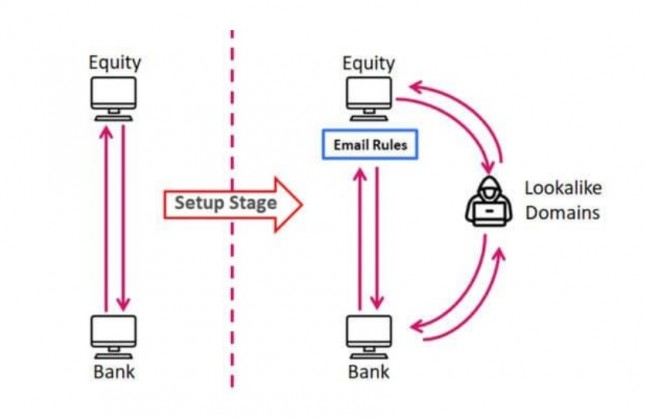
In a sophisticated BEC attack recently exposed by Check Point Research, the attackers infiltrated the o365 email account of three financial firms and monitored all correspondence for several weeks. They then created lookalike domains for the attacked firms, as well as the corresponding partners, accountants and banks, and then diverted relevant communication to the fake domains.
This created a “man-in-the-middle” scheme (Fig 1) which allowed them to divert and initiate fraudulent money transfers of more than US$1.3 million. Such attacks are more complicated to terminate even after their exposure since an unknown number of customers and service providers may still be unknowingly conducting correspondence directly with the attackers.
Intervention in such operations requires international law enforcement cooperation in networks spread over several continents. One such operation, revealed in September 2019, resulted in the arrest of 281 suspects located in 10 countries, as well as the recovery of US$120 million in confiscated and recovered wire transfers.
Direct money transfers are not the only way to steal money through BEC attacks. In many cases, it is easier to persuade company officials to buy gift cards rather than make a direct fund transfer. In this way, attackers are not required to create fraudulent bank accounts and gift card details can be sold online in forums for about 70% of their actual value.
Attacks with gift cards are especially widespread during holiday seasons and getting money back is nearly impossible. The most popular gift card suppliers used in BEC frauds are Google Play, eBay, Target, and Walmart and according to researchers, this technology is used in more than 60% of BEC accidents.
Read Also
MoreLogin, the World's #1 Antidetect Browser, Showcased at Affiliate…
Experts gather in Nanning to support high-quality development of…
Huawei Garners Award from Manpower Ministry as Best Foreign Enterprise…
Government's Role in Consumer Protection in the Digital Era
Huawei Supplier Convention 2023: Driving Collaboration and Innovation…
Today's Industry

Selasa, 23 April 2024 - 10:29 WIB
President Jokowi Reaffirms Commitment to Farmers’ Welfare
President Joko “Jokowi” Widodo on Monday (04/22) inspected corn harvest in Boalemo regency, Gorontalo province. “Our corn import has decreased significantly from 3.5 million tonnes to…

Rabu, 28 Februari 2024 - 12:47 WIB
Carsurin and NBRI Strengthen Strategic Alliance to Propel Indonesia’s EV Industry
PT Carsurin Tbk ("Carsurin") and the National Battery Research Institute ("NBRI") are pleased to announce the signing of a pivotal Strategic Alliance Agreement (SAA), marking a significant advancement…

Rabu, 21 Februari 2024 - 08:43 WIB
Gov’t to Continue Disbursing Rice Assistance
President Joko “Jokowi” Widodo has ensured that the Government will continue rolling out the rice assistance program for low-income families. The President made the statement when handing…

Rabu, 21 Februari 2024 - 08:40 WIB
Bapanas Head Ensures Availability of Rice Stock Ahead of Ramadan
The National Food Agency (Bapanas) has ensured the availability of rice for the fasting month of Ramadan and Eid al-Fitr 1445 Hijri/2024 CE. “We believe that there is enough rice for the fasting…

Rabu, 21 Februari 2024 - 08:23 WIB
Receives Chairman of Jababeka (KIJA), Menpora Dito Ready to Support the Development of Sports SEZs
Chairman of PT Jababeka Tbk (KIJA), Setyono Djuandi Darmono met the Minister of Youth and Sports of the Republic of Indonesia (Menpora RI) Dito Ariotedjo at the Kemenpora RI Office, Senayan,…

















News Comment